Why We Built Shield: Closing the Security Gap in Cloud Networking
The "why" behind moving beyond standard proxies to build a HIPAA-compliant solution that never needs to decrypt your traffic or expose your network infrastructure.
Learn when to prioritize speed (SSL Termination) and when strict compliance requires end-to-end security (SSL Passthrough).
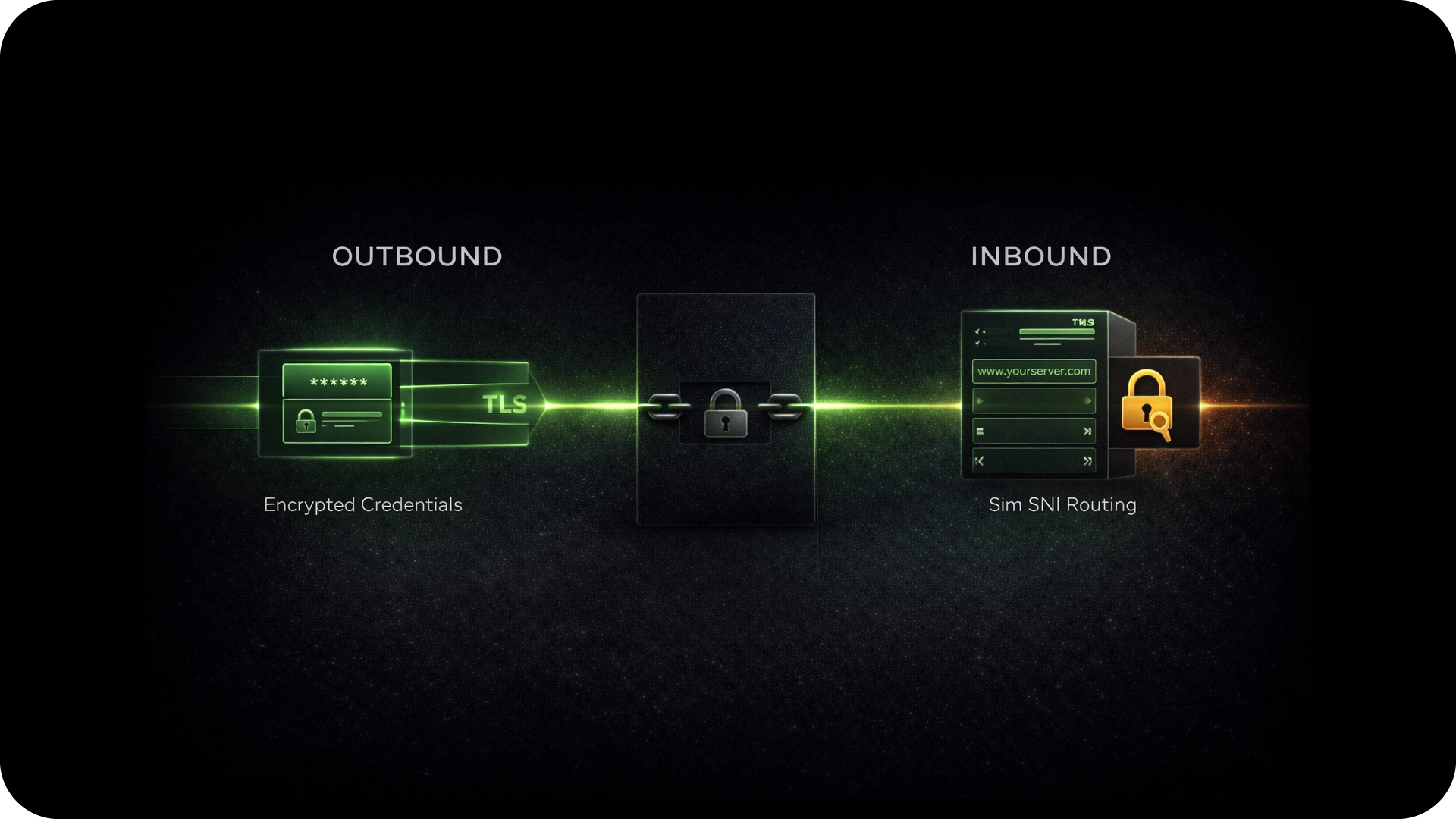
The Mechanics of End-to-End Encryption
How Shield guarantees compliance without compromising connectivity.
Outbound: Encrypted Credentials
Standard proxies send passwords in plain text. Shield wraps authentication headers in TLS, so your credentials remain secure from end-to-end.
Inbound: Smart SNI Routing
We use Server Name Indication (SNI) to route inbound traffic without unwrapping packets. Decryption happens solely on your server, never on ours.
No Private Keys
We architecturally reject SSL certificates. Since we never hold your private keys, we cannot read your data, even in the event of a total system compromise.
FAQs
Common questions about encryption, compliance, and security specifics.
Shield’s HTTPS and Secure SOCKS outbound service can be used with many languages directly or with our QGPass wrapper program.
When using HTTPS requests through the HTTPS proxy, the data is encrypted from end to end (like an HTTP proxy) and your credentials to the proxy are encrypted as well (unlike an HTTP proxy) and the data is never decrypted at any point in the journey (to include endpoints) because we do not maintain the private key of the sending/receiving organization(s).
Shield’s inbound proxy uses SSL passthrough. When sending an HTTPS request through the QG Shield inbound proxies, the HTTP data is encrypted end to end.
We use SNI to route your requests to the correct location, so there is no need to give us your SSL certificates and your data is never decrypted at any endpoints (for the same reason) because we do not have the private key of the sending/receiving organization(s).
Regardless of HTTP (QG Static) vs HTTPS proxy (QG Shield), if you are connecting to an HTTPS server through the proxy, the data itself is encrypted from end to end, but the authentication credentials, final destination hostname, and port would still be in the clear with any other proxy service.
Yes.
Because QuotaGuard Shield uses SSL Passthrough, we function strictly as a "conduit" under HIPAA guidelines. We route your encrypted traffic without ever decrypting it, meaning we have zero access to PHI (Protected Health Information) or PII (Personally Identifiable Information).
This architecture satisfies the strict 'transmission security' requirements of HIPAA, PCI-DSS, and SOC 2 by ensuring your data remains fully opaque to us and maintaining End-to-End Encryption from your server to its final destination.
No.
With Shield, you manage your certificates exactly as you do now, on your own server or PaaS (Heroku, AWS, Azure). You do not upload keys to QuotaGuard.
Since we do not terminate the connection, your existing SSL configuration works transparently through our proxy.
This eliminates the security risk (and administrative headache) of sharing private keys with a third-party vendor.
Yes, but your IP addresses and connection string will change. Keep that in mind if you plan on changing in the future.
Our Support can help you switch from QuotaGuard Static to Shield at any time with zero downtime.
While the connection URL format changes slightly (to enable the passthrough protocol), your underlying network architecture requires no re-engineering.
We often recommend developers start with Static for speed and cost-efficiency during development, then upgrade to Shield as the application moves to production or undergoes security audits. Just be aware those production IPs will be different (which in many cases is a benefit).
While we cannot inspect your encrypted payload (the body of your data), we can still analyze the connection metadata.
Our engineers can verify the TCP handshake, TLS version negotiation, and upstream termination codes.
This allows us to pinpoint firewall rejections, timeout issues, or certificate mismatches without ever needing to decrypt or view your sensitive application data.
Still have questions?
We don’t outsource Support to non-engineers.
Reach out directly to the engineers who built Shield to discuss your specific architecture, integration challenges, or compliance constraints here.
🚀 Ready to Get Started? Choose Your QuotaGuard Path
QuotaGuard STATIC
QuotaGuard SHIELD
Reliability Engineered for the Modern Cloud
For over a decade, QuotaGuard has provided reliable, high-performance static IP and proxy solutions for cloud environments like Heroku, Kubernetes, and AWS.
Get the fixed identity and security your application needs today.




