The One-Click Solution for Heroku Static IPs
Secure, Load-Balanced Static IP Addresses for Your Heroku Apps, Heroku's preferred Static IP partner since 2013
The Trusted Foundation: Reliability, Speed, and Support
All QuotaGuard solutions are built on a decade of experience and a high-availability architecture designed to scale with your business.
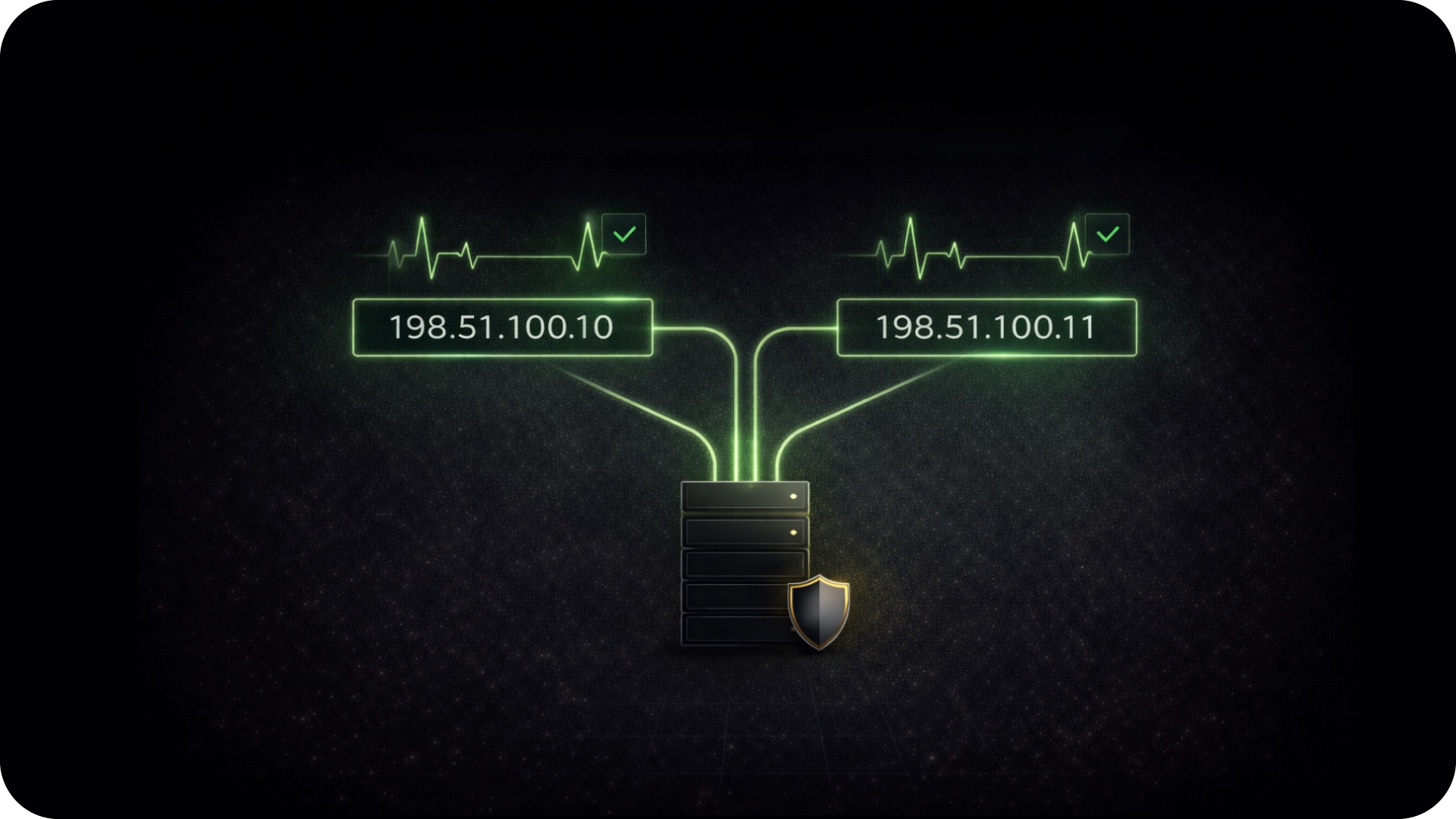
Load Balanced Pair of Static IPs
Each subscription has a load balanced pair of static IP addresses. If one IP fails, traffic automatically routes through your second IP with health checks and automated failover, guaranteeing zero downtime and zero manual intervention.
Ultra-Low Latency and Global Reach
You select what app region you want for ultra low latency. Our proxies run on all Heroku regions, ensuring your traffic stays fast regardless of your Heroku dyno location.
Demonstrated Reliability & Scalability
QuotaGuard has maintained 99.98% uptime since 2013. With over 32,327 Heroku customers served since 2013, we provide a solution that is trusted and proven to scale.
FAQs
Common questions about Heroku Static IPs and QuotaGuard.
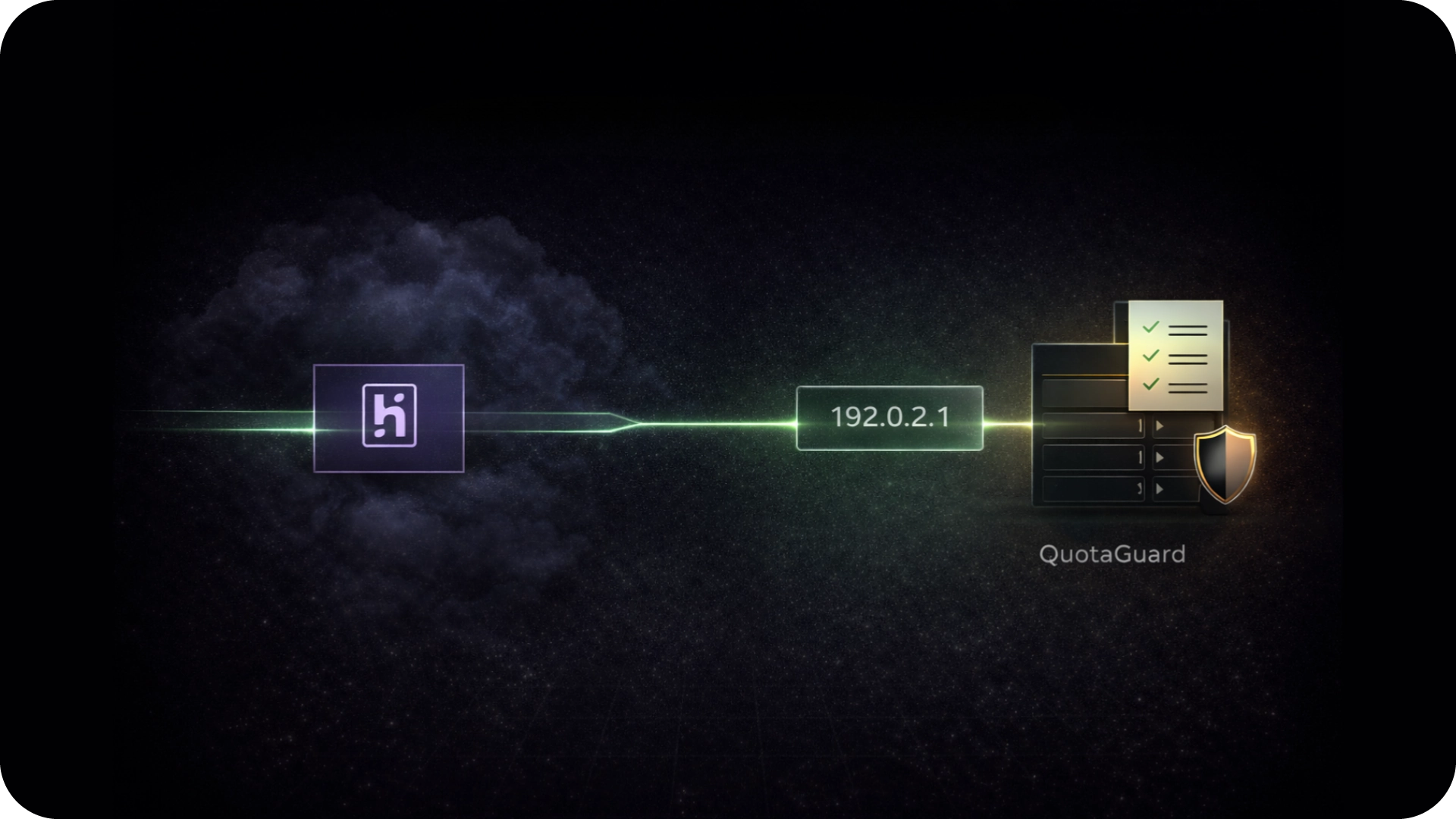
QuotaGuard is available directly on the Heroku Add-Ons marketplace.
You can configure your Static IP addresses to your Heroku app in a single click, with no need to change the core of your application code.
You simply tweak your Heroku connection config code to direct requests through our provided proxy server.
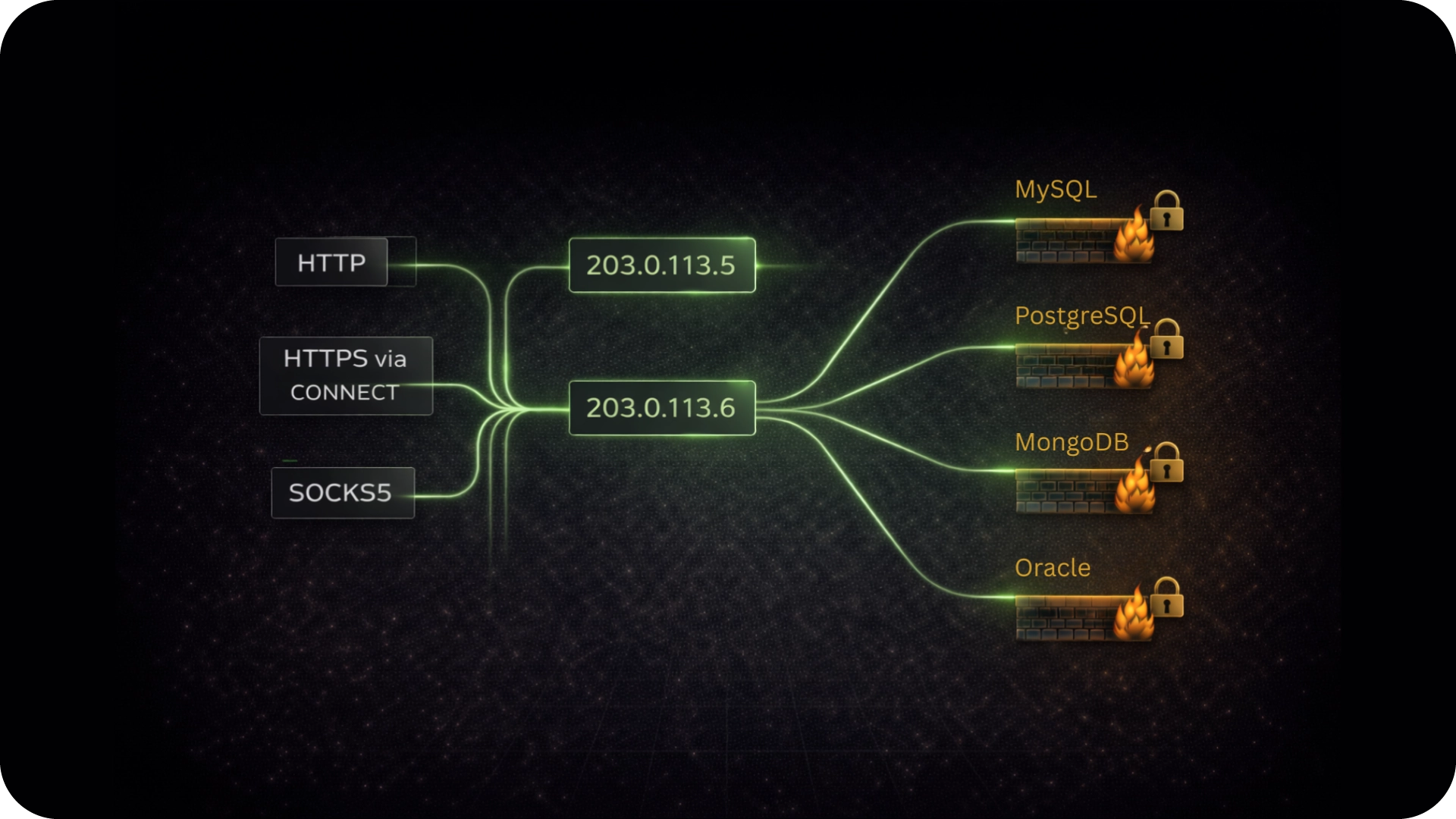
QuotaGuard Static is the Builder's Choice, focused on flexibility, speed, and securing standard API connections.
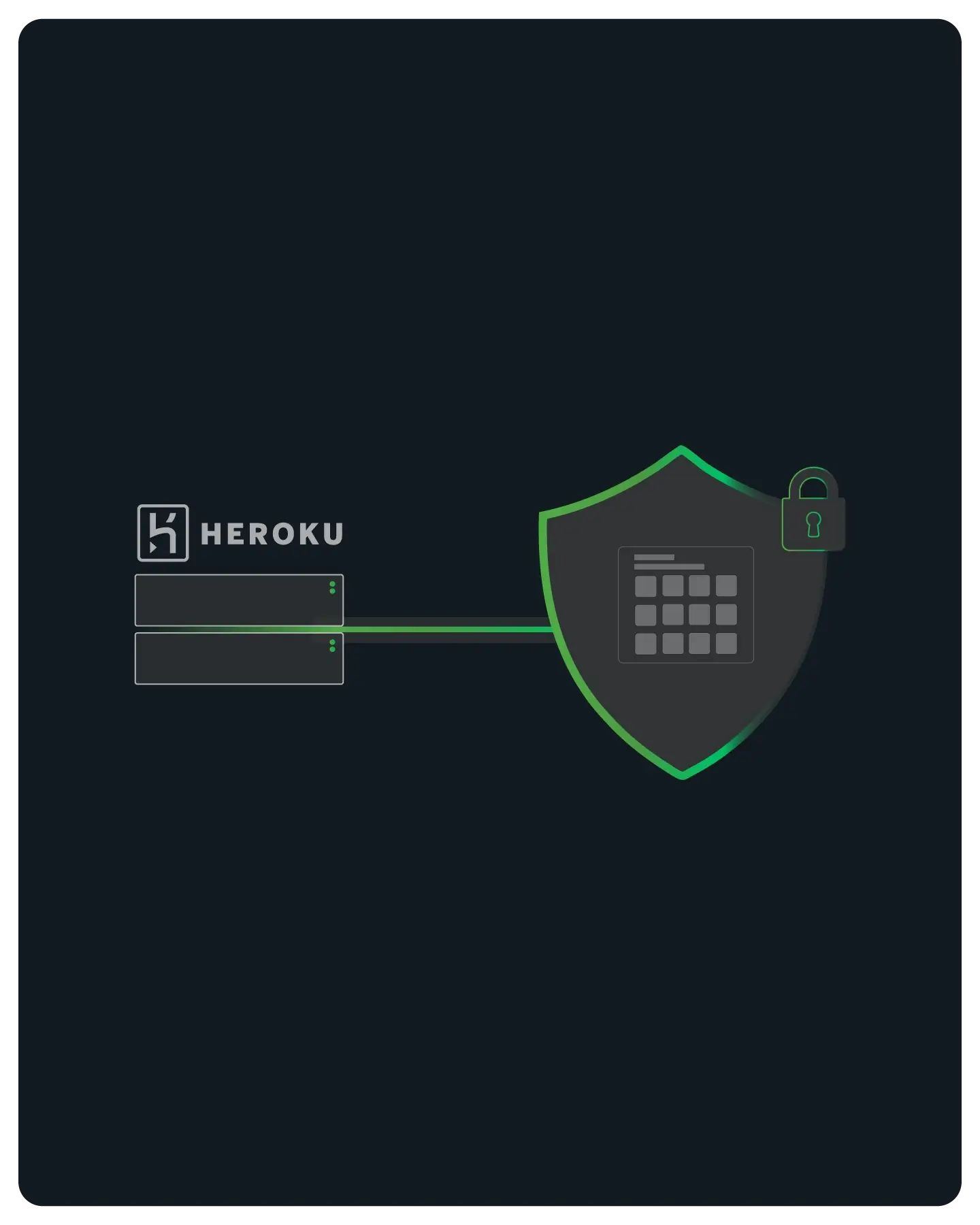
QuotaGuard Shield is the Buyer's Choice, offering end-to-end security with SSL Passthrough and an architecture designed specifically to meet strict HIPAA and PCI compliance requirements.
We go into greater detail at "Why is QuotaGuard Shield More Secure Than QuotaGuard Static?"
No.
Your Static IP Addresses will not change when you upgrade or downgrade your usage plan.
This is critical because we know you have already whitelisted them everywhere.
We operate with a "No Hard Stops" policy.
If your app exceeds your current usage limit, we will keep processing your requests and will reach out to you to discuss an upgrade.
Please read more about this policy at our Soft Policy documentation.
No. There is no minimum commitment.
You can upgrade, downgrade, or cancel your account at any time with zero hassle, no long-term contracts, and no cancellation fees.
You can expect Professional and Responsive Support from full-time QuotaGuard engineers, not AI bots, "side project" engineers, or outsourced support staff.
We pride ourselves on having real engineers debug connectivity issues with you, not chatbots reading scripts.
We offer one-on-one setup assistance, and our average response time is under 2 hours.
Still have questions?
We don’t outsource Support to non-engineers.
Reach out directly to the engineers who built QuotaGuard to discuss your specific architecture, integration challenges, or compliance constraints here.
🚀 Ready to Get Started? Choose Your QuotaGuard Path
QuotaGuard STATIC
QuotaGuard SHIELD
Trusted by Engineering Teams Everywhere
Reliability Engineered for the Modern Cloud
For over a decade, QuotaGuard has provided reliable, high-performance static IP and proxy solutions for cloud environments like Heroku, Kubernetes, and AWS.
Get the fixed identity and security your application needs today.